Navigation
DEF CON 33 More Stats
DEF CON 33 - Here’s some data
This year, sparky and mac wanted to start sharing a bit more of what we do and how things go behind the scene. In that sense, I am going to throw at you a lot of boring numbers, charts… and some fun stuff we did this year.
First we do the work
Like mac mentioned on his post, this year we knew beforehand that we would have less time to setup everything. So we had to be creative and come up with ways to reduce our setup time, and one of those ideas was to use wireless bridges to significantly reduce the number of physical drops we had to run all over the convention center.
On Monday, we got together in a hotel space and worked as a team to pre-stage as much of the equipment as possible, that included the 62 wireless bridges we were going to deploy all over LVCC.
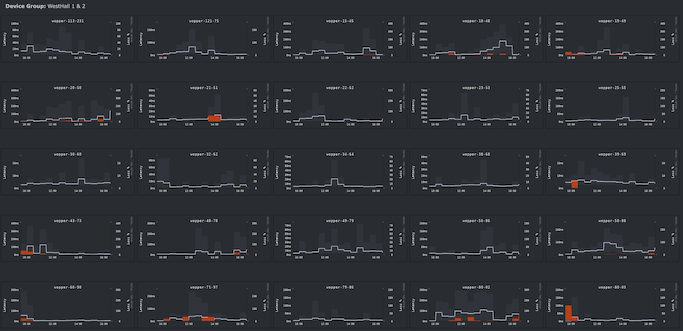
We were excited to see how well those wireless bridges would work… and as you can see on the graphs below, they worked surprisingly well, considering the busy environment.
And yes, we heard a good number of folks were complaining about the wireless network. But I wanted to take this moment to clarify that as far as data goes, the wireless network was actually rock solid, low latency and all that good stuff. We did have one issue Saturday afternoon, where the DHCP decided to take a nap and made it look like the DefCon wireless networks were offline. That lasted about 20 minutes before everything was up and running again. So when folks rightfully complained about “the wifi” on social media, read our internet pipes, and not the wireless itself. Our friends that take care of the wireless networks felt the heat while doing their best, so I wanted to clear that up. Give them some love, they did an amazing job.
The Woppers
That’s what we called those wireless bridges internally, “woppers”.
As you can see below, our average “last mile” latency, which is basically latency between the wopper and the other side of the wireless network, was below 20ms, with sub-10ms on a good chunk of them. For this kind of busy environment, that is pretty solid. The “reds” you see are packet losses, and we were monitoring these closely throughout the day. When we saw them, we went to physically check on the wopper, and 100% of the time was due to people moving them under tables or even under other objects/bags. For next year that is something we plan to address by sticking them to high poles or similar.
Then we have fun
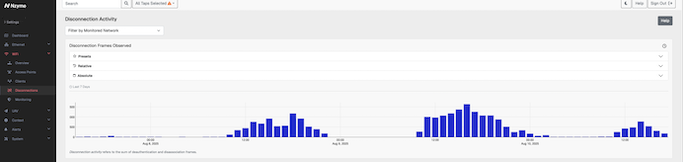
This year we deployed some extra monitoring around the LVCC to see what you all were up to… and you didn’t disappoint us! Good job! We were using Nzyme for this.
Good news first, we didn’t see any significant/relevant de-auth attacks on the wireless network. As you can see on the graph below, there is no “spike” in de-auths, other than the expected from normal activities. And to be honest, if you are connect to the WPA3-only network, sans an RF blast on all frequencies, you are safe from those kind of attacks. I am not saying people didn’t try, it was just not enough to cause any trouble.
This is DEF CON
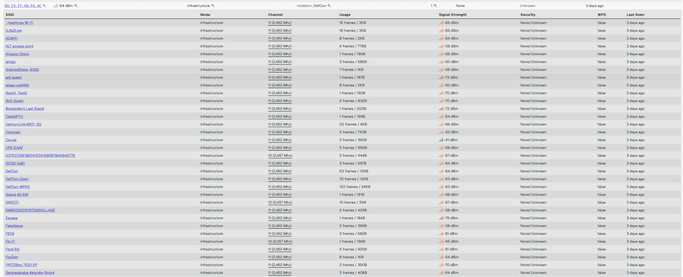
When they say out there this is a hostile environment… this is what they mean. We of course had folks blasting around all kinds of SSIDs, like “Comcast”, “Ford-5G”, airport lobby, stores… you name it. As you probably understands, your phone WILL automatically connect to those networks if you ever connected to them and left the “Remember Network” box checked… which is no bueno.
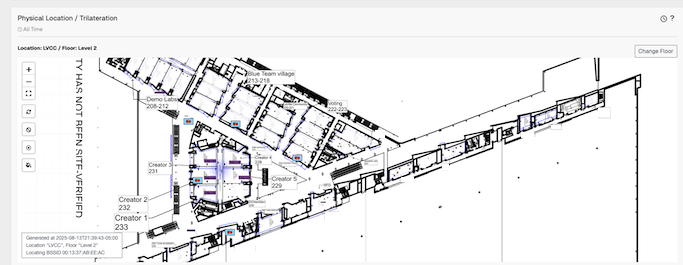
And by the way, trilateration works and we could pinpoint where those funny people were. ;)
Someone (or multiple people?) also dropped ESP32s all over the LVCC. I did some reverse engineering on the firmware to see what was going on. They were basically broadcasting a network with the same name as DefCon-Open, counting how many users connected to it, and they could also setup a fake captive portal with a password form that redirected to a page that played Rick Astley’s famous song.
Lastly, here are some other interesting things we were able to see:
Rogue devices:
ESP32 Marauders (not unique devices, but times we saw them advertising): 11486
Unique Pwnagotchi: 23
Unique Flipper Zero Evil Portal: 12
Unique Wifi Pineapples: 34
Fake Doppelgangers of our Networks:
Networks with same name as Defcon Secure Networks but disabled encryption (Unique sources): 10
Networks with similar name as Defcon networks (Unique sources): 5
Other stats:
UAVs (drones) sending beacons around LVCC West: 86
Management Frames processed in bytes: 26,360,159,156 (26GB)
Peak number of devices advertising networks around LVCC: 6023
Interesting SSIDs
Before I list them, a few remarks:
Yes, there is a Dunkin' Donuts at the LVCC. No, they don't have a free wifi network without a captive portal!Our open network is DefCon-Open, not DEFCON OPEN... I recommend you connect to neither...Good old Rick Roll is back this year...
SpaceLasers
iPhone
Dunkin' Donuts Guest
It Hurts When IP
You shall not connect
IG Labs Regional Airport_5G
FakeNews
IG Labs Regional Airport
01 Never gonna give you up
02 Never gonna let you down
03 Never gonna run around
04 and desert you
08 and hurt you
07 Never gonna tell a lie
05 Never gonna make you cry
06 Never gonna say goodbye
"Nock, nock, Luke."
FBI Van #4
House LANister
FBI-surveillance-van
DEFCON OPEN
FBI Surveillance Van
NSA_Surveillance
NSAsurveillanceVan01
Even with all the challenges, it was a good year. And I can’t wait for DEF CON 34!!
– strange